1. List and describe an organization’s three communities of interest that engage in efforts to solve InfoSec problems. Give two or three examples of who might be in each community.
The three defined communities are decision makers in Information security, Information technology and non-technical staff. Examples of Information security professionals could include a risk manager or the CISO. The information technology group could include the CIO or a systems administrator. Some examples of Non-technical members could be the CEO or the Director of Human Resources.
2. What is the definition of Information Security? What essential protections must be in place to protect information systems from danger?
From the lecture material: “The protection of information and its critical elements (confidentiality, integrity and availability), including the systems and hardware that use, store, and transmit that information” Essential protections that must be in place include physical security, operations security, communications security and network security.
3. What is the C.I.A. triangle? Define each of its component parts.
- Confidentiality -only those who are granted access can get in
- Integrity- data is true and uncorrupted
- Availability – if granted access, data is available without obstruction
4. Describe the CNSS security model. What are its three dimensions?
• The McCumber Cube is a comprehensive information security model that covers the three dimensions of information security – the CIA triangle, data states (storage, processing and transmission) and controls (policy education and technology).
5. What is the definition of privacy as it relates to information security? How is this definition of privacy different from the everyday definition? Why is this difference significant?
The text describes privacy as “Information that is collected, used and stored by an organization is intended only for the purposes stated by the data owner at the time it was collected” and a dictionary describes it as “the state of being free from intrusion or disturbance in one’s private life or affairs”. The expectation of privacy does not extend into the Information Security model; it does not guarantee freedom from observation, only that any data gathered will be used in an expected and declared manner.
6. Define the InfoSec processes of identification, authentication, authorization and accountability.
- Identification –An individual user or process is named and unique
- Authentication – A control verifies that he user is who they say they are, usually possessing something they have (example a certificate) or something they know (example: a password)
- Authorization – Explicit permission to an identifiable and authenticated user has been granted to access a resource.
- Accountability- A user or processes’ actions can be logged or otherwise tied back to the originating account.
7. What is management and what is a manager? What roles do manager play as they execute their responsibilities?
From the lecture notes: Management is “The process of achieving objectives using a given set of resources “A manager is “Someone who works with and through other people by coordinating their work activities in order to accomplish organizational goals“. Managers use different roles to accomplish objectives. In an informational role, managers collect process and use information. In an interpersonal role, managers work with people to achieve goals. In a decisional role, managers make choices as to the best path to take and address issues that arise while using problem solving skills.
8. How are leadership and management similar? How are they different?
Good leadership and management are intertwined. Management focuses on the planning and strategic decisions, and leadership provides the motivation to implement the planning and organizing functions.
9. What are the characteristics of management based on the popular approach to management? Define each characteristic.
The popular approach to management includes
- Planning- Goals, objectives, strategizing and plans
- Organizing- Structure, Human resource allocation
- Leading- Motivation, leading, communication, group dynamics
- Controlling- Standards, measurement, comparisons, action
10. What are the three types of general planning? Define each.
- Strategic Planning- Long term goals, 5 or more years
- Tactical Planning- Production planning, one to five years, smaller scope then enterprise planning
- Operational Planning – Day to day operations, short term goals.
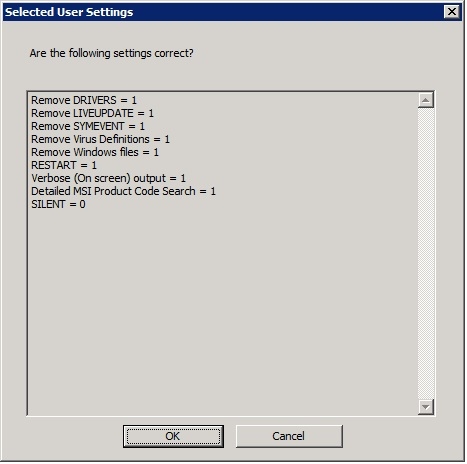
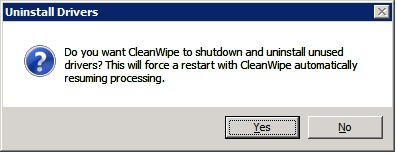 Similar to the earlier product ‘nonav’, running Symantec’s Cleanwipe is simple, just follow along with the prompts as they appear, then allow the machine to reboot when finished.
Similar to the earlier product ‘nonav’, running Symantec’s Cleanwipe is simple, just follow along with the prompts as they appear, then allow the machine to reboot when finished.